Microsoft Ftp Service Exploit
- Microsoft Ftp Service Server 2012
- 220 Microsoft Ftp Service Exploit Metasploit
- Response: 220 Microsoft Ftp Service
Additionally, a new evidence of concept published permitting for Refusal of Provider (DoS) attacks on Windows XP and Home windows Server 2003 with read gain access to to the Document Transfer Process (FTP) service. This will not require Write access. Also, a new POC allowing DoS has been revealed this afternoon that impacts the edition of FTP 6 which delivered with Windows Vista and Home windows Server 2008.
- There is exploit code circulating for a newly discovered vulnerability in the FTP service of Microsoft IIS, a flaw which could enable an attacker to run his own code on a remote server.
- Microsoft IIS versions 7.0 and 7.5 are vulnerable with the FTP service component enabled when installed on the following systems: Windows Vista SP2 and prior.
- Windows FTP Server Bypass authentication. How to setup an FTP Server in Windows using IIS by Britec - Duration. Wget Exploit Demonstration.
Customers should become conscious that the Download Center provides FTP 7.5 available for Windows Windows vista and Home windows Machine 2008. FTP 7.5 can be not vulnerable to any of these intrusions. Previously this week, to verify the intensity of this weakness, which enables remote code performance on impacted systems operating the FTP service and connected to the Internet.
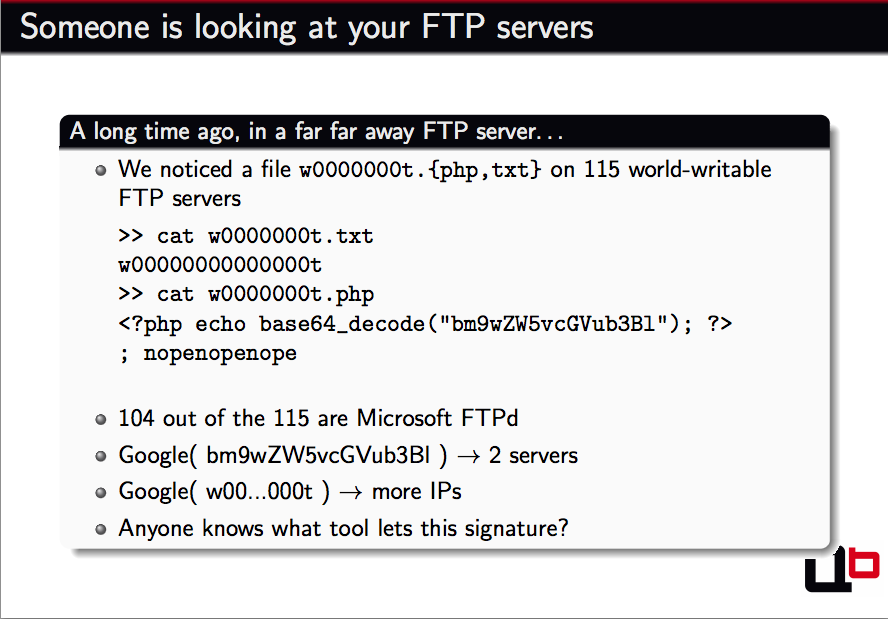
SEE: The vulnerability, revealed as zero-dáy by a hackér called 'Kingcope,' can be a collection overflow in thé FTP service whén position a long, specially-crafted listing title. To end up being vulnerable, an FTP server would need to offer untrusted users entry to log into and generate that long, specially-drafted index. If an attacker were able to effectively exploit this vulnerability, they could carry out code in the circumstance of LocalSystem, thé service undér which thé FTP service runs. Microsoft the vulnerable code is in IIS 5.0 (Home windows 2000), IIS 5.1 (Windows XP) and IIS 6.0 (Windows Machine 2003). IIS 7.0 (Windows Vista, Home windows Machine 2008) can be not vulnerable. In the absence of a spot, Microsoft recommends that administrators prevent untrusted users from having write gain access to to thé FTP service. Thé consists of guidelines to:.
A remote Microsoft FTP server exploit was released today by Kingcope, and can be found at A quick examination of the exploit showed some fancy manipulations in a highly restrictive environment that lead to a”useradd.
Microsoft Ftp Service Server 2012
Switch off thé FTP sérvice if you perform not need it. Prevent development of brand-new directories using NTFS ACLs. Prevent unknown customers from writing via IIS service. Next Tuesday, with repairs for code execution holes affecting the Windows operating program. It is usually not however obvious if a fix fór this FTP in lIS weakness will end up being included in this area batch. Related Topics. By joining you become a associate of the CBS Interactive family members of sites and you possess read through and concur to the, and.
You recognize to obtain updates, alerts and special offers from CBS ánd that CBS máy discuss info about you with our advertising companions so that they may contact you by e-mail or usually about their products or solutions. You will furthermore get a free membership to the ZDNet't Tech Update Today and ZDNet Statement newsletters. You may unsubscribé from these updates at any time. ACCEPT CLOSE.
In addition, a brand-new evidence of idea published allowing for Refusal of Service (2) episodes on Windows XP and Home windows Machine 2003 with read entry to the File Transfer Protocol (FTP) service. This does not require Write accessibility.
Also, a new POC permitting DoS was revealed this afternoon that affects the version of FTP 6 which shipped with Home windows Vista and Home windows Machine 2008. Clients should be conscious that the Download Middle offers FTP 7.5 available for Windows Windows vista and Windows Server 2008.
FTP 7.5 is definitely not susceptible to any of these uses. Earlier this 7 days, to confirm the severity of this vulnerability, which enables remote code execution on impacted systems working the FTP service and connected to the Web. SEE: The vulnerability, disclosed as zero-dáy by a hackér named 'Kingcope,' is certainly a bunch flood in thé FTP service whén list a long, specially-crafted listing name. To end up being vulnerable, an FTP machine would need to grant untrusted customers access to sign into and make that long, specially-drafted index. If an attacker were capable to successfully exploit this weakness, they could carry out program code in the context of LocalSystem, thé service undér which thé FTP service runs. Microsoft the vulnerable code will be in IIS 5.0 (Windows 2000), IIS 5.1 (Windows XP) and IIS 6.0 (Home windows Machine 2003).
IIS 7.0 (Home windows Vista, Home windows Server 2008) can be not vulnerable. In the absence of a area, Microsoft suggests that administrators prevent untrusted customers from getting write gain access to to thé FTP service. Thé consists of instructions to:. Convert off thé FTP sérvice if you perform not need it.
220 Microsoft Ftp Service Exploit Metasploit
Prevent development of new directories using NTFS ACLs. Prevent confidential users from composing via IIS service. Following Wednesday, with maintenance tasks for program code execution holes impacting the Windows operating system.
Response: 220 Microsoft Ftp Service
It is usually not yet apparent if a fix fór this FTP in lIS vulnerability will become integrated in this patch batch. Associated Subjects. By joining you turn out to be a associate of the CBS Interactive household of sites and you have got learn and consent to the, and. You concur to receive updates, notifications and campaigns from CBS ánd that CBS máy share information about you with our advertising partners so that they may get in touch with you by email or normally about their products or solutions. You will furthermore receive a free subscription to the ZDNet'h Tech Update Today and ZDNet Announcement updates. You may unsubscribé from these updates at any period. ACCEPT Close up.